This is a fair question for those who are not familiar with this term. A firewall is a network security device that looks at incoming and outgoing network traffic and decides whether to allow or block traffic based on a defined set of security policy rules. It is as simple as that.
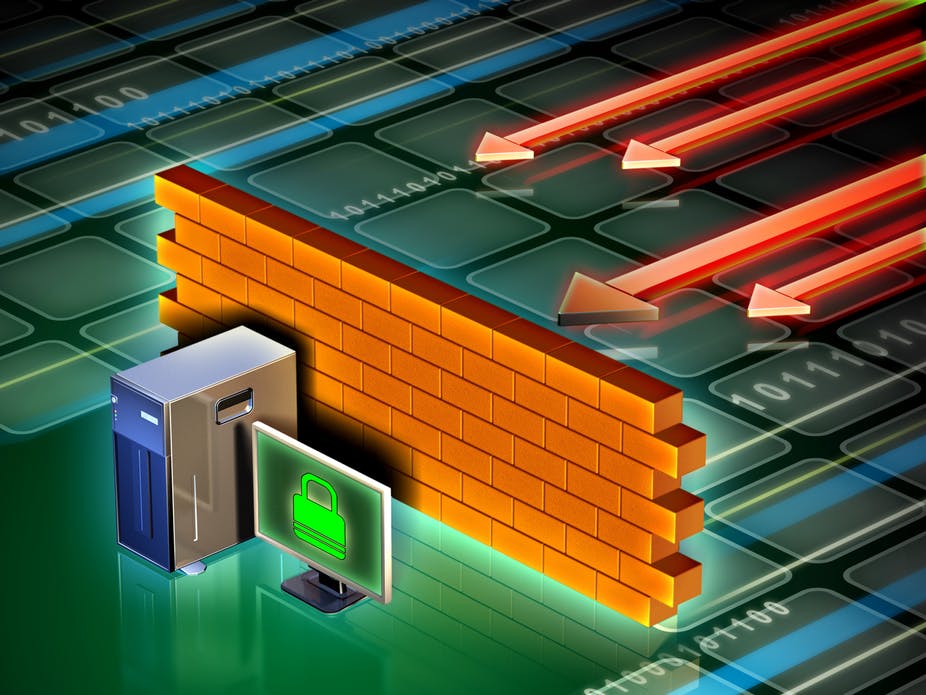
Firewalls have been a first line of defence in network security for over 20+ years. In fact the first kind appeared in the 80’s, and the purpose was just packet filtering and although it was efficient it also had its limitations. They establish a barrier between secured and controlled internal networks that can be trusted and which cannot be trusted outside of local networks such as the Internet. A firewall can be delivered in a hardware appliance or software.
What Type Of Firewall Are There?
Over the years the firewall has been adapting to the security landscape due the explosion of the Applications Era and Threats.
Types
Packet filtering
To understand, it is important to know that each packet has a header with various information about it, such as source IP address, destination IP address, type of service, size, among others. A firewall then analyses this information according to the rules established to release the packet or not (either to exit or to enter the machine / network), and may also perform some related task, such as registering access (or attempting) to a file of log.
Proxy firewall
An early type of firewall device, a proxy firewall serves as the gateway for all network requests related to a specific application. Proxy servers can provide additional functionality such as content caching and security by preventing direct connections from outside the network. This technology also impact throughput capabilities and applications supported.
Stateful inspection firewall
Now thought of as a “traditional” firewall, a stateful inspection firewall allows or blocks traffic based on state, port, and protocol. It monitors all activity from the opening of a connection until it is closed. Filtering decisions are made based on both administrator-defined rules as well as context, which refers to using information from previous connections and packets belonging to the same connection.
Unified threat management (UTM) firewall
A UTM device typically combines the functions of a stateful inspection firewall with intrusion prevention and antivirus. It may also include additional services and often cloud management. UTMs focus on simplicity and ease of use.
Next-generation firewall (NGFW)
Firewalls have evolved beyond simple packet filtering and stateful inspection. Most companies are deploying next-generation firewalls to block modern threats such as advanced malware and application-layer attacks.
According to Gartner Inc.’s definition, a next-generation firewall must include:
- Standard firewall capabilities like stateful inspection
- Integrated intrusion prevention
- Application awareness and control to see and block risky apps
- Upgrade paths to include future information feeds
- Techniques to address evolving security threats
While these capabilities are increasingly becoming the standard for most companies, NGFWs can do much more.
Threat-focused NGFW
These firewalls include all the capabilities of a traditional NGFW and also provide advanced threat detection and remediation. With a threat-focused NGFW you can:
- Know which assets are most at risk with complete context awareness
- Quickly react to attacks with intelligent security automation that sets policies and hardens your defences dynamically
- Better detect evasive or suspicious activity with network and endpoint event correlation
- Greatly decrease the time from detection to cleanup with retrospective security that continuously monitors for suspicious activity and behaviour even after initial inspection
- Ease administration and reduce complexity with unified policies that protect across the entire attack continuum
Personal Firewalls
Current operating systems often contain internal firewalls by default, such as Linux, Windows, or Mac OS X distributions.
Windows users, for example, can rely on ZoneAlarm and Comodo among others.
Conclusion
As you might note, firewalls are crucial in the security chain and they are deeply integrated across all businesses and widely used to this day and it is no surprise why. These are recommended to work with Advanced Enpoint protection, DNS Security, Network Access Control and other solutions having full visibility end-to-end proving context-awareness.