Manufacturer Usage Descriptions otherwise known as “MUD” facilitate’s device visibility and segmentation by allowing your network administrators to effortlessly identify a specific type of IoT device and then define the appropriate behaviors for that device. IoT manufacturers are able to disclose to us what devices are on the network, and what network policies they need for the devices to correctly function. This whitelist statement is something that customers can use to deploy access policies in their own networks without any guesswork.

How MUD Works
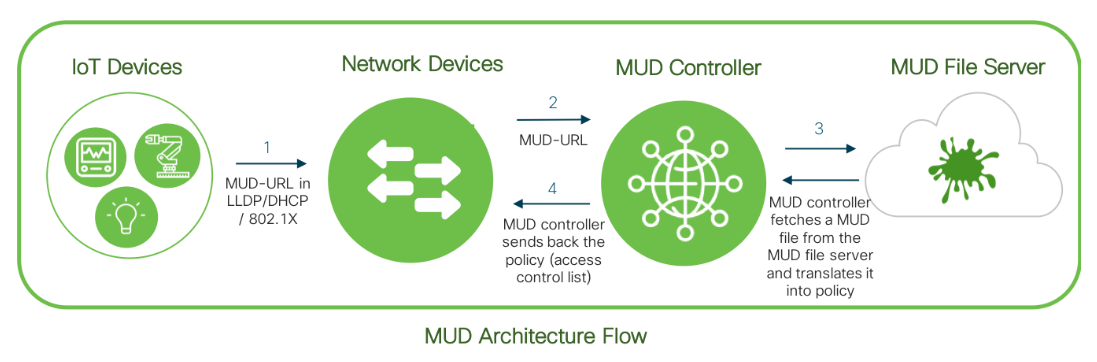
An IoT device first sends out a pre-embedded MUD-URL to the network devices (e.g. switch & AAA server), through which the MUD-URL will be received by the MUD controller (software). According to the specific MUD-URL, a matching MUD file will be provided from the MUD file server and translated into policy format through the Manufacturer Usage Description controller, to then enforce the access control list to the device.
The Cisco Identity Services Engine (ISE) offers a network-based approach for adaptable, trusted access everywhere, based on context. It gives you intelligent, integrated protection through intent-based policy and compliance solutions.
Benefits to Customers and Manufacturers Alike with MUD
Manufacturers and Customers are two key variables in the MUD ecosystem. MUD offers different benefits for customers and manufactures alike:
Benefits to customers:
- Automate IoT device type identification which reduces operational costs
- Simplify and scale IoT device access management by automating the policy enforcement process
- Reduce threat surface of exploding number of IoT devices by regulating traffic and therefore avoid lateral infections
- Secure your network through standard-based approach
Benefits to manufacturers:
- Improve customer satisfaction and adoption due to reduced operational costs and security risks
- Enhance device security through standard-based on-boarding procedure
- Differentiate device offerings with embedded network-based device security feature
- Reduce product support costs to customers by following an easy-to-implement process
MUD creates a standard method for manufacturers to specify both device identity and the recommended communication patterns for that device type. The 10,000 feet view of the MUD process is shown here in the diagram below:
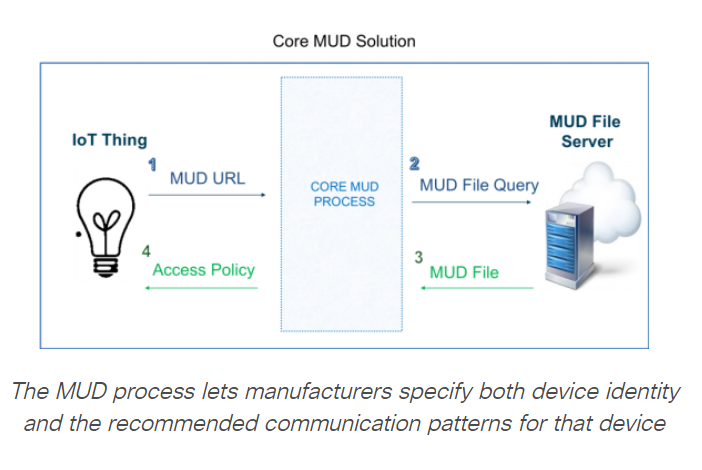
In simplified terms, the manufacturer of a device can embed a url into the device itself, which is picked up by a core MUD process when the device initially connects to a network. The MUD process classifies the device based on this url, and fetches it’s recommended communication patterns from an internet available MUD file server that the url also points to. This abstracted policy is then applied to the access point that the IoT Device is connected to.