Ransomware is a type of malicious software (malware) created to block access to files or systems and is often only released after a payment in Digital Currency (e.g Bitcoin) to scammers. You can call this digital blackmail.
Ransomware: The Hijackers
The term ‘Ransomware’ developed its name because it is quite literally software which scammers install to demand a ransom to be paid on your hardware. Despite being seen as a recent security problem, ransomware is not a new concept: the first examples of this type of activity dates back to as early as the 1980’s.
Casino malware is a memory resident, it immediately infects the copy of COMMAND.COM located in the C: drive root directory and It infects .COM files when any of three events occur: If the system user issues a DIR command, or a file does an internal DIR command, one .COM file in the current directory is infected. Additionally, if the system user executes an infected file, a .COM file becomes infected. Casino infects .COM files that are opened by another file so you can see just how easy it is for this virus to spread quickly infecting more files.
Casino would execute itself on the 15th of every month starting in April affecting people who often play online gambling games, it copied the FAT file system to RAM and erases all data on the local computer hard drive if the user didn’t play the game or even if the user restarted their computer.
How Ransomware Spreads
Ransomware didn’t replace other methods used to spread viruses and other malware: e-mails, social networks (Facebook, Twitter), instant messaging services (WhatsApp, Skype) and fake sites are still the most commonly used for this kind of activity.
In almost all ransomware is a social engineering tactic, there is a misleading link which appeals to a user and when they follow the link on the other side is ultimately ransomware. The text can say, for example, that you have unpaid debt, a bank security update or an invitation to view intimate photos of a famous personality. Notice how these texts try to scare the user or capture his curiosity, it is often fear which makes individuals follow these links unknowingly. After following the link a high percentage of these people will then click a follow up link to install malicious ransomware.
Ransomware is commonly delivered as an antivirus, game or application which can seem appealing. In many cases a user will click on pages or links promoting ‘free security downloads’ or ‘PC speed accelerators’ and it is the promise of a free service which often catches so many users out. When you install the ransomware you eventually allow the malware to infect your computer or mobile device by granting it access to your personal documents. There are cases of ransomware attacks that exploit operating systems, applications or plug-in failures (such as Java and Flash), however social engineering and email ransomware attacks have a far wider reach. Think, for example, that you received an email from an e-commerce store advising that your order is out for delivery but it turns out that you did not even make any purchases! Clicks are driven by curiosity so the promise of a service or information which may improve your computer or knowledge is what catches so many of us off
Would you ever click? A lot of people fell to this tactic in 2016 to a ransomware called Locky. In that case the emails were in the name of Amazon, one of the best-known e-commerce stores in the world.
How the Ransomwares act
After the contamination, ransomware make its first move by executing instructions that will block access to all files encrypting them. Even though the data is still on the computer the ransomware is there to block all access to the files.
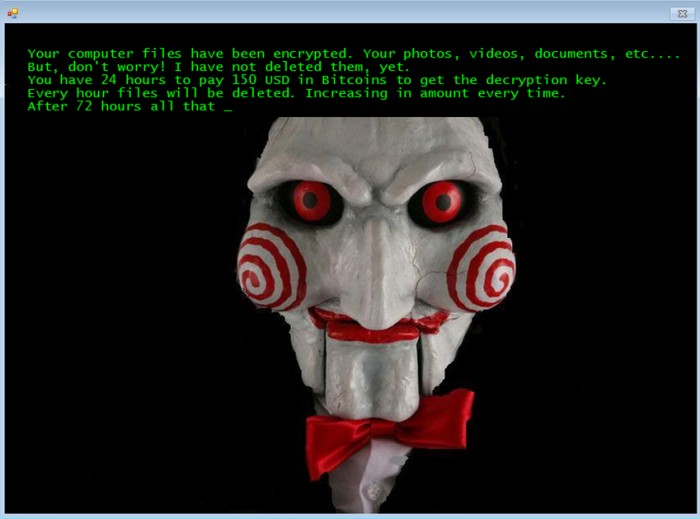
To put pressure on the user some lock screens even display a counter saying that if payment is not made until such a time then all files will be deleted. A ransomware called Jigsaw (inspired by the movie “Jigsaw”), identified in 2016, acted like this: the user had 72 hours to make the payment; every hour, a part of the computers data was deleted similarly to the film where if a task was not completed in a certain time then there would be fatal consequences.
A screen locking ransomware that became relatively famous is ‘WinLock’ which emerged in Russia in 2010. The lock displayed a message with an erotic image and required the user to use an SMS payment system worth $10 to be free and therefore save themselves the embarrassment of having erotic images stuck on their computer for all to see. The people responsible for WinLock were arrested (after making $ 16 million with the scheme).
The Next Generation of Ransomware
The next generation of ransomware has already received the name of: crypto-ransomware. Computers and mobile devices (tablets and smartphones) now have enough processing power to encrypt files quickly and only the attacker has the cryptographic keys used in the attack, it is very difficult for the victim to recover the affected files.
Another strength of crypto-ransomware is that even when they are removed from the operating system, the encrypted files remain that way, therefore the chances of the user giving up and paying increases considerably to try and save their device.
The Worst Cybersecurity Ransomware Attacks
One of the best-known crypto-ransomware attacks was CryptoLocker (2013), which used up to 2048-bit RSA-type encryption. When this malware blocked data it displayed a message on the screen informing that the user would only have their files back (documents, photos, videos, etc.) after a payment was recieved completely bricking devices.
The WannaCry ransomware attack (2017) targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments through Bitcoin cryptocurrency. It propagated through EternalBlue, an exploit developed by the USA Agency (NSA) for older Windows systems (Win XP) that was released by Shadow Brokers (Hacker Group) a few months prior to the attack. While Microsoft had released patches previously to close the exploit, much of WannaCry’s spread was from organisations that had not applied these patches or they were using older Windows systems that were past their end-of-life. WannaCry also took advantage of installing backdoors onto infected systems. The National Health Service (NHS) in the UK was massively affected having to shutdown systems, creating a chaotic scenario for patients with much of their personal data compromised. A report published by the government estimates the ransomware caused approximately £19m of lost output and £73m in IT costs. Some £72m was spent on restoring systems and data in the weeks after the attack.
The attack was stopped within a few days of its discovery due to emergency patches released by Microsoft, and the discovery of a kill switch that prevented infected computers from spreading WannaCry further. The attack was estimated to have affected more than 200,000 computers across 150 countries, with total damages ranging from hundreds of millions to billions of dollars. Security experts believed from preliminary evaluation of the worm that the attack originated from North Korea or agencies working for the country.
Conclusion
This kind of attacks gets worse when Enterprise Systems servers critical to a business are attacked: as no user can access the system this completely prevents the application from working. To bring back the entire Infrastructure using backups is not an easy task due the Terabytes of data lost in such a short time frame and businesses cannot afford to stop functioning as so many only operate online. We recommend our clients to start with our tailored Security Assessment so we can identify and mitigate the blind spots, therefore building a resilient Incident Response Plan
Anatomy of an Attack – Inside the Mind of a Hacker
Click to watch an interesting video into the Anatomy of an Attack.